CASA Summer School
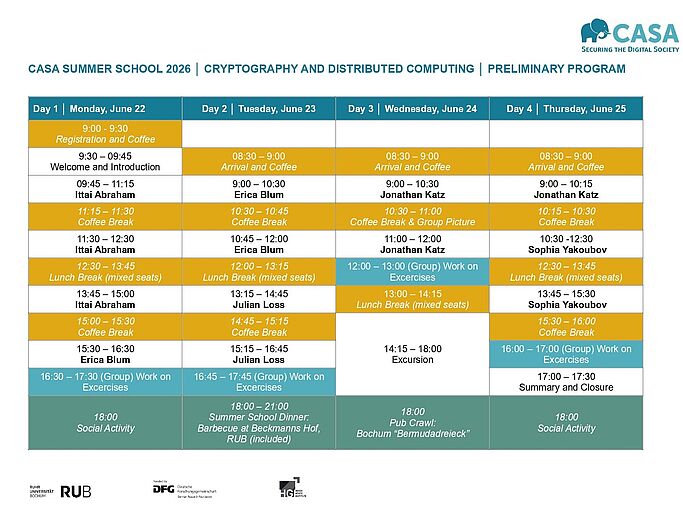
The CASA Summer School is an annual event that offers young researchers interesting lectures by high-ranking speakers and the opportunity for international exchange. We cordially invite PhD students, postdoctoral researchers, master's students, and advanced bachelor's students close to graduation from the field of cyber security to participate. They can qualify in advance through an application process.